2 May 2024 | By Jesse Brett
Embracing the AI Revolution with Microsoft 365 Copilot
Copilot offers significant productivity gains, but before embracing the AI Revolution, businesses must lay a secure foundation for optimal use.
Read moreMore than £4bn was stolen in the UK by fraudsters and cyber criminals in 2022, according to a recent report[1] — a staggering 63% increase in losses compared to 2021. And with new, high-profile cyber attacks in the headlines daily, it’s clear that cyber crime is on the rise. Whether simple phishing scams or sophisticated, targeted breaches that could cripple a company’s operations and reputation, prioritising a robust, layered security posture has never been so important.
But while many businesses have some safeguards in place, how can they be confident that they’re truly protected?
A cyber security framework (CSF) is a set of best practices, standards and recommendations designed to help an organisation improve its cyber security posture. Performing an independent cyber security review against an established CSF is an essential step for strengthening and verifying your security strategy. This can give a strong indication of an organisation’s current position and prevent two of the most common cyber security pitfalls:
Poor investments
Using a CSF can ensure that further security investments are the right ones. Without this framework, businesses risk making poor decisions about what products, services and solutions they truly need.
A false sense of security
Without identifying your specific vulnerabilities, it can be challenging to understand the cyber risks you face. Using a CSF ensures you’re best placed to implement the right solutions for your business.
Not only can a CSF validate an organisation’s existing capabilities, but it can also be used to identify any gaps and open up wider considerations.
So, how do you create a solid defence for your business?
This is where the National Institute of Standards and Technology (NIST) comes in. NIST’s CSF is widely considered the ‘gold standard’, although it shares many elements with other international standards and frameworks such as ISO 27001 and the Center for Internet Security (CIS). The NIST CSF is based on five core functions laid out in the diagram below. Let’s dig deeper…
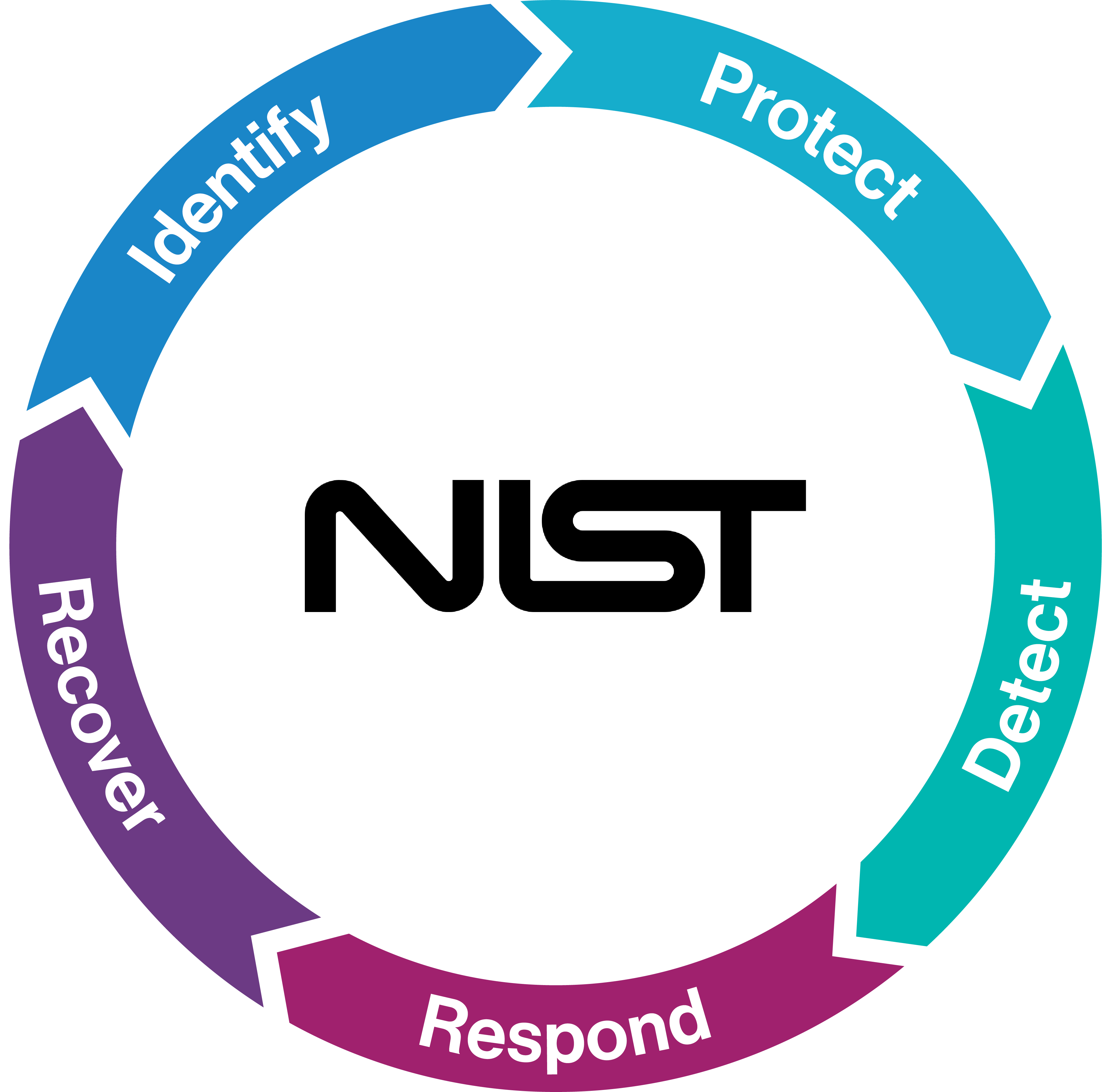
Identify
Few businesses maintain a comprehensive list of the devices on their network. From TVs and entry systems to environmental sensors and thermostats, 100% visibility of your IT ecosystem is a prerequisite to an effective security posture. Only when you truly understand what you need to protect can you start to layer the solutions and services to fulfil that requirement.
Although this may seem like a lot of manual work, it should be considered necessary due diligence as it lays the foundation for a robust strategy. And because both businesses and threats are continually evolving, regularly revisiting and updating this inventory is crucial to enable your businesses to focus and prioritise its efforts — and put the right tools in place.
Protect
The aim of the Protect function is to develop safeguards that prevent a cyber security incident and support the ability to contain any impact should one occur. The most effective way to do this is to follow a ‘defence-in-depth’ strategy, which involves layering a series of defensive mechanisms that protect valuable data and information.
Examples of different protection layers include antivirus, firewall, email filtering, multi-factor authentication (MFA) and ongoing employee awareness training — all deliberate steps to lock down your environment against the risk and threat of potential cyber attacks.
Traditionally, these safeguards have been seen as the most important part of a cyber security strategy, but that viewpoint needs to change. A robust, fit-for-purpose strategy will incorporate elements of all five pillars.
Detect
In today’s threat landscape, someone will inevitably find their way through your defence at some point. And when they do, your business needs to be ready for it.
The Detect function is perhaps the most important — and most overlooked — function of the NIST framework, ensuring the timely discovery of any anomalies or suspicious activity before a threat actor achieves their goal. The sooner a threat is detected, the sooner your business can respond. The detection layer is comprised of continuous monitoring, visibility and logging, and the data must be proactively interrogated to ensure early detection.
Respond
The Respond function focuses on taking appropriate action once a threat has been detected. This requires proactive procedures such as an Incident Response Plan, unique to your business, which instructs on how to respond to a serious security incident and who has which responsibilities.
This plan can have a significant impact on the speed and completeness of recovery — so how you respond can be what makes or breaks your business.
It’s worth mentioning Managed Extended Detection and Response (MXDR) here, as we’re seeing more and more companies incorporating this into their cyber security strategy. In fact, now considered ‘best practice’, Gartner predicts that 50% of organisations will be using MDR services by 2025[2]. This service involves outsourcing the combined Detect and Respond functions to dedicated 24/7/365 security specialists — often with the advantage of their own custom threat intelligence — who investigate alerts and incidents and assist in remediation where necessary. We’ll be covering MXDR in more detail in our next blog, so watch this space.
Recover
Failing to prepare for an attack could have devastating consequences for a business, so Business Continuity and Disaster Recovery plans are essential. This layer should include following established recovery plans, tested backups, table top exercises to build resilience, and having readily available contact details for your business’ cyber insurance provider and incident response partner.
Ultimately, both the risks and the tools available to mitigate them are constantly changing, so your business’ cyber security strategy is something that should continuously be reviewed and adjusted. Working in alignment with an established CSF can identify the strengths and weaknesses of your cyber security posture — and demonstrates that your business has taken the necessary steps to protect itself and its customers. To find out more about how we can help develop your cyber security strategy, call us today on 03330 33 22 55.
[1] Fraudsters and cyber criminals stole more than £4bn in the UK through 2022 | Computer Weekly
[2] Market Guide for Managed Detection and Response Services | Gartner