2 May 2024 | By Jesse Brett
Embracing the AI Revolution with Microsoft 365 Copilot
Copilot offers significant productivity gains, but before embracing the AI Revolution, businesses must lay a secure foundation for optimal use.
Read moreIn the current business climate, we’re constantly seeing high-profile media reports about major breaches that occurred where basic security patches had not been installed. In many cases, these high-priority updates had been available for months or, in a few cases, years. Yet, IT departments had not deployed them. And when 60% of breaches are linked to a known vulnerability where a patch is available but not applied1, it raises the question: why?
According to the National Institute of Standards and Technology (NIST), over 20,000 new vulnerabilities were identified across 20212. Keeping on top of them could be more than one person’s full-time job — but not every vulnerability represents a threat. Given that only around 2% are actually exploitable3, how can you be certain whether your business is even affected in the first place? This is where vulnerability management fits into your cyber security strategy.
A critical aspect of any ‘defence-in-depth’ security posture, vulnerability management is the ongoing process of identifying, assessing and remediating vulnerabilities across your IT estate to reduce the likelihood of being compromised.
Businesses aren’t typically targeted by ‘zero-day’ attacks, which exploit vulnerabilities that don’t yet have a patch available. Instead, it’s much more common for threat actors to rely on an organisation’s delay in patching. The importance of timely patching is reflected by this year’s overhaul of the government-backed Cyber Essentials certification, which now specifies that patches must be applied within 14 days of being made available.
With that in mind, what makes a solid vulnerability management strategy?
At its core, there are three essential components:
Here’s why…
An effective vulnerability management approach starts with taking a complete inventory of all devices on the network. Due to today’s distributed workforce, the attack surface now extends beyond the traditional network perimeter — users, devices and apps are now ‘everywhere’, and this must be taken into consideration when drawing up a comprehensive and accurate inventory to work from.
Only when you truly understand what you need to protect can you establish a powerful vulnerability management strategy.
Traditionally, many companies have relied on an annual penetration test or external infrastructure assessment to discover whether they’ve been exposed, often due to compliance requirements. But the constantly changing nature of today’s threat landscape — with new vulnerabilities discovered daily — requires a more responsive strategy to avoid leaving the door open to an attack in the time between tests.
This is where technology can help.
Continuous vulnerability testing is an ongoing process of regular, automated scans designed to alert your business about known vulnerabilities before they can be exploited and weaponised. Armed with this knowledge, an organisation can then proactively execute their remediation strategy, ensuring they remain one step ahead.
And when it comes to remediation, relying on time-consuming manual patching is simply unrealistic for most IT teams, especially given both the rising number of vulnerabilities and the raft of devices across organisations. It can be a challenge to balance the need to mitigate vulnerabilities with the need to keep systems running — all while ensuring new patches are compatible.
To address these challenges, organisations are turning to automated patch management processes. Using the right tools, it’s possible to create policy-based rules for the prioritisation and application of patches and schedule their deployment outside of business hours to minimise downtime while reducing complexity.
One of the many benefits of migrating to the public cloud is that it transfers some of the risk and security responsibility to the cloud provider. The ‘shared responsibility’ model of the public cloud defines which responsibilities are that of the cloud provider and that of your business.
This can complement a vulnerability management strategy that incorporates the previously defined elements by delegating responsibility for patch management to a trusted cloud provider. As shown in the table below, the SaaS model allows you to delegate the most responsibility and gain the most advantage of the available security benefits for the services consumed.
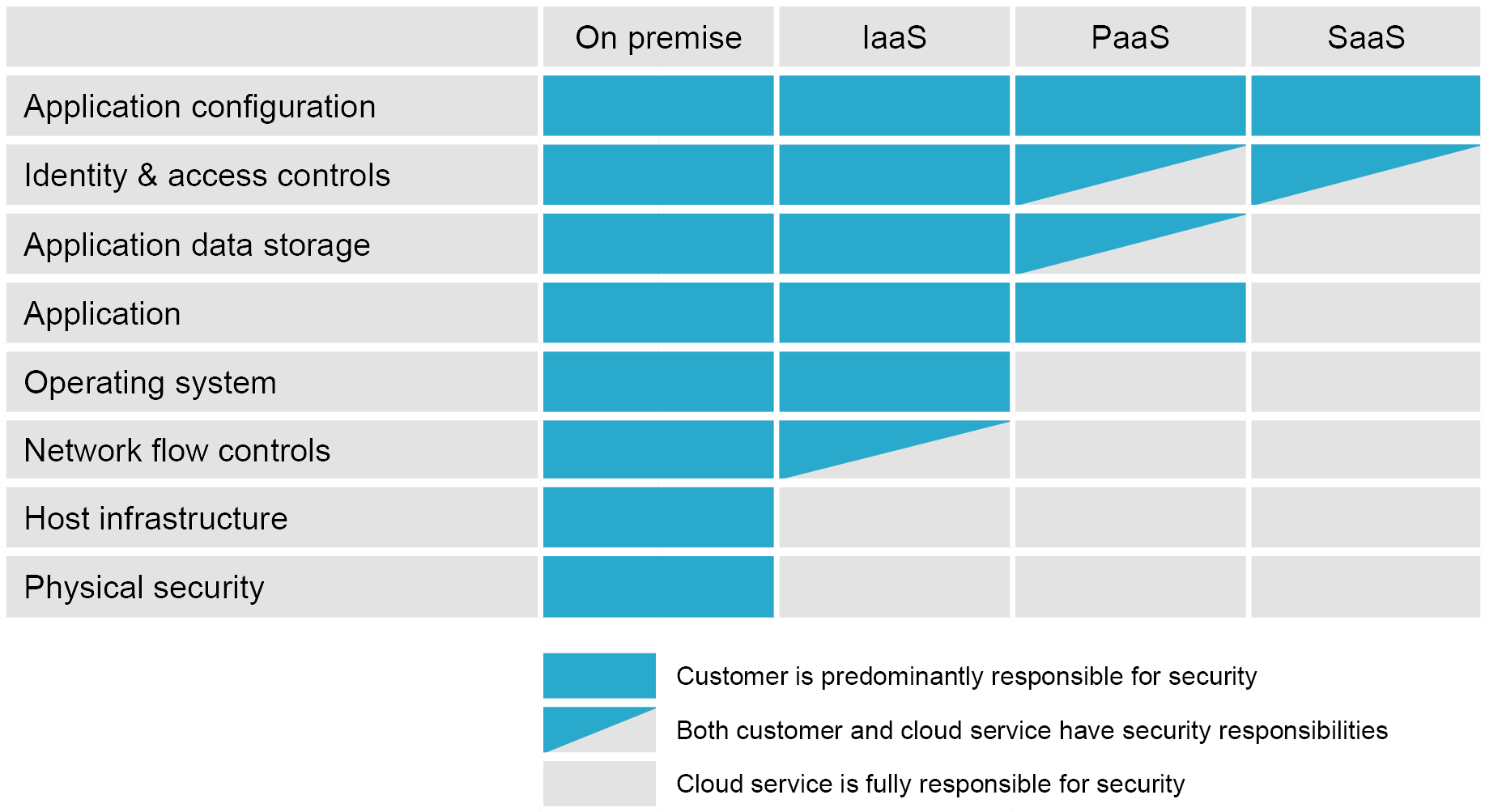
Ultimately, a continuous, automated strategy that incorporates live patch management, regular vulnerability scanning and risk transfer is essential to any proactive cyber security approach. Bistech has proven knowledge and experience to guide you through the vulnerability management minefield — leaving you to focus on your business. Call us today on 03330 11 22 55.
1 Ponemon Institute, 2019, ‘Costs and Consequences of Gaps in Vulnerability Response’
2 NIST, 2022, ‘National Vulnerability Database: CVSS Severity Distribution Over Time’
3 Rebasoft, 2022, ‘Continuous Vulnerability Assessment’